For any organisation, being continually familiar with its confidential information as well as its locations can sometimes be a challenge!
A growing number of organisations have discovered the advantages and efficacy of bringing files together by storing them and sharing them in the centralised environment offered by Teams collaborative solution. Microsoft has invested massively in homogenising and centralising collaborative functions so as to simplify their use and facilitate their adoption by end users. This trend allows organisations to have a global vision of their data protection and compliance.
A practical approach to evaluate the maturity of compliance would be to identify, as much as possible, the level of sensitivity of the data and define the most critical subjects for the organisation inorder to set a search method for the priority documents to be classified.
Meanwhile, the correlation between the strategy and the target governance of the organisation must be taken into consideration.
The real challenges of data protection are:
Correctly associating technologies to reach their objectives
Validating legal authorisation for the right to inspect data
Getting direct accessibility to tools and results
To do this, the Microsoft 365 functionalities and the Cloud Azure services necessary for compliance objectives should be evaluated, depending on the licence level held by the organisation. This evaluation should be regularly refined to benefit from the new features added by Microsoft to its Microsoft 365 offer. By their level of granularity and their completeness, the features offered by Microsoft allow end to end control of data protection, and thus strengthen the compliance of the organisation’s infrastructure.
To carry out this process, the 4 stages to maintain and stabilise are:
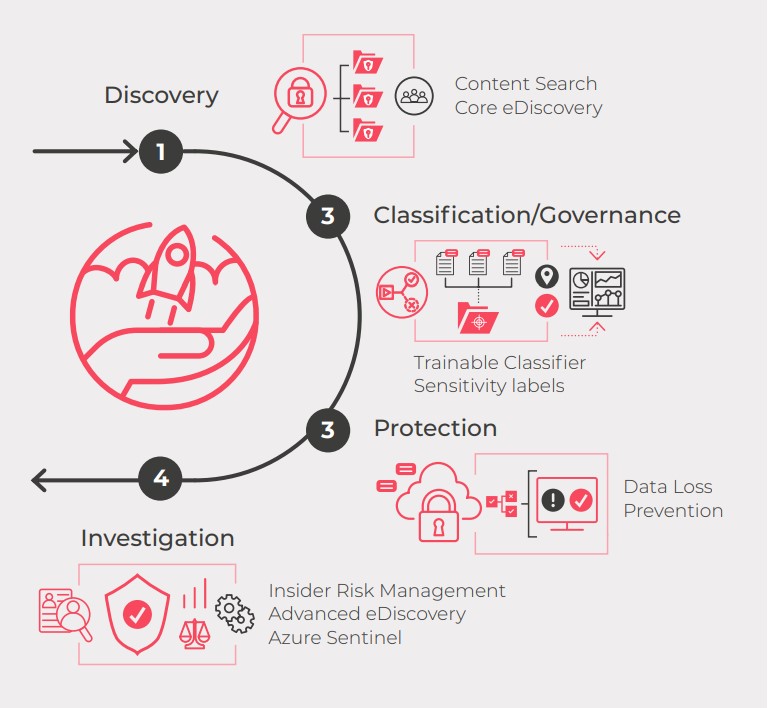
1. Discovery
Firstly, a map of the organisation’s infrastructure should be created, by studying all the internal documents relating to compliance, as well as the different classification and data protection policies.
This inventory gives a good theoretical vision of what protection level the set of documents present in Microsoft 365 tenant should have. In practice, this phase consists of reassembling a list of documents not aligned with the compliance policy, or with the standards of the organisation.
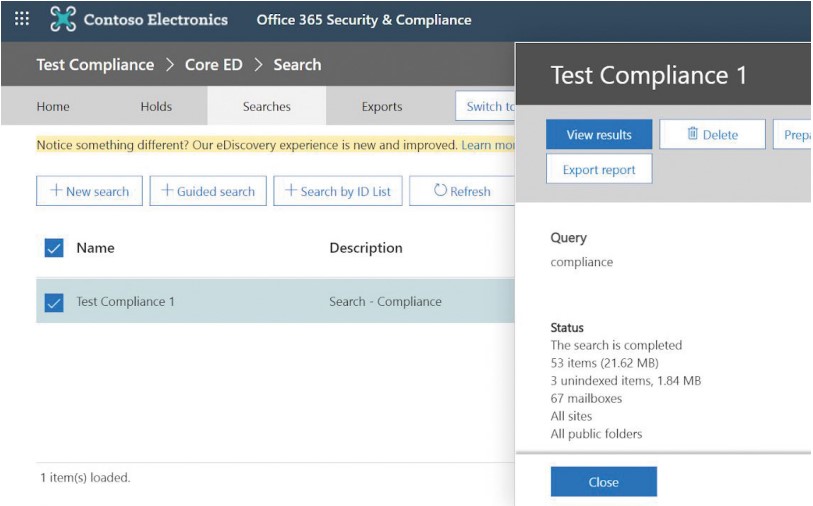
The Microsoft Compliance Centre offers this problem, through two functionalities:
- Content search: Allows content in electronic messages, documents and conversations to be found by a single search, through guided or customisable searches.
- Core eDiscovery: Offers the same features as the Content Search tool and results can serve as evidence during legal cases. eDiscovery exports are encrypted by security measures and can be analysed via the Advanced eDiscovery tool.
Searches by keywords should be precise to limit searches to the most relevant documents, and it is often essential to finetune these searches by iterations, in order to get a usable result (conditions, key words, specific or global locations).
This method creates a key words lexicon which can be reused regularly, and constantly enriched to maintain a good evaluation level of the compliance maturity of the Microsoft 365 tenant.
2. Classification/Governance
Classifying its documents using labels and governing them with dashboards, is crucial for a company in order to protect themselves. Labels allow traceability and control of information, whether stored or in transit. An exhaustive classification allows analysis of data flows to detect abnormal behaviour and take appropriate corrective measures.
Trainable Classifier
Given the high number of documents processed by each body, to industrialise and systematically process classification, the Trainable Classifier* is a Machine Learning tool which learns to recognise all types of documents: emails, web formats and Microsoft Office suite documents.
To start the process, the organisation provides a sample of several hundred distinct elements so Machine Learning can make forecasts based on the data entered. These results should be confirmed by the organisation to fine-tune their forecasts, sorting false positives and negatives, enabling them to find, classify and label documents appropriately.
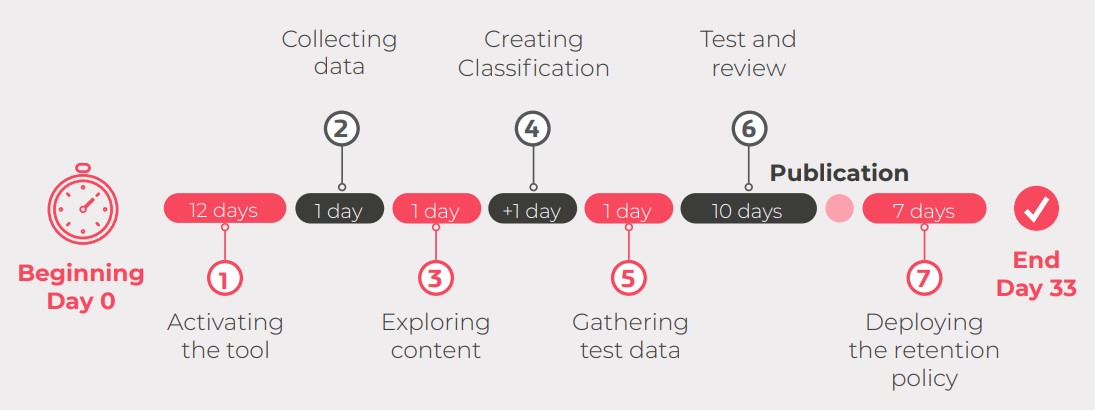
Optimal implementation of the Trainable Classifier solution requires a 33 day period following Microsoft’s forecasts and recommendations.
This solution can also be used at the “Classification – Governance” stage as well as at the previous “Discovery” stage.
To complement a classification project, an overall view of the organisation’s maturity level is possible through the Compliance Centre which allows data to be governed globally.
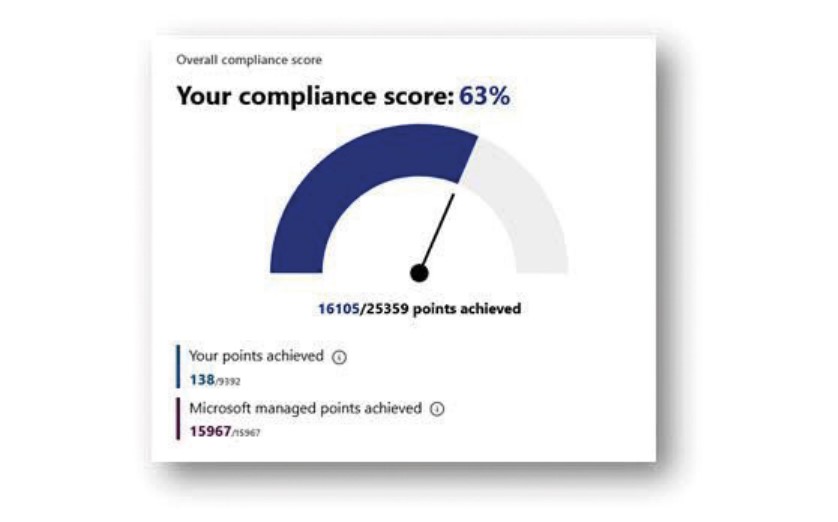
The Compliance Centre offers different dashboards identifying and synthesizing information related to the organisation’s compliance. These allow visualisation of the global compliance score calculated on the basis of Microsoft’s recommendations and suggestions for improvement.
A list of remediation actions that can improve the maturity compliance level is provided and each action improves the global compliance score.
This sensitivity level is determined through the Sensitive Info Types function of Microsoft Information Protection, allowing recognition of a level of document sensitivity according to data structure, based on regular expressions or a lexicon of keywords (for example identity card, passport or credit card numbers).
The addition of different levels of sensitivity supports the definition of storage, use and communication rules in the M365 tenant.
3. Protection
Once non-compliances are identified and documents are correctly classified, the next phase involves protecting information detected as sensitive.
To benefit from labeling and strengthen data protection, Microsoft’s Data Loss Prevention (DLP) tool allows written warnings on the strategies base concerning Sensitive Info Types, as well as data protection rules linked to documents or the mailbox according to their criticality.
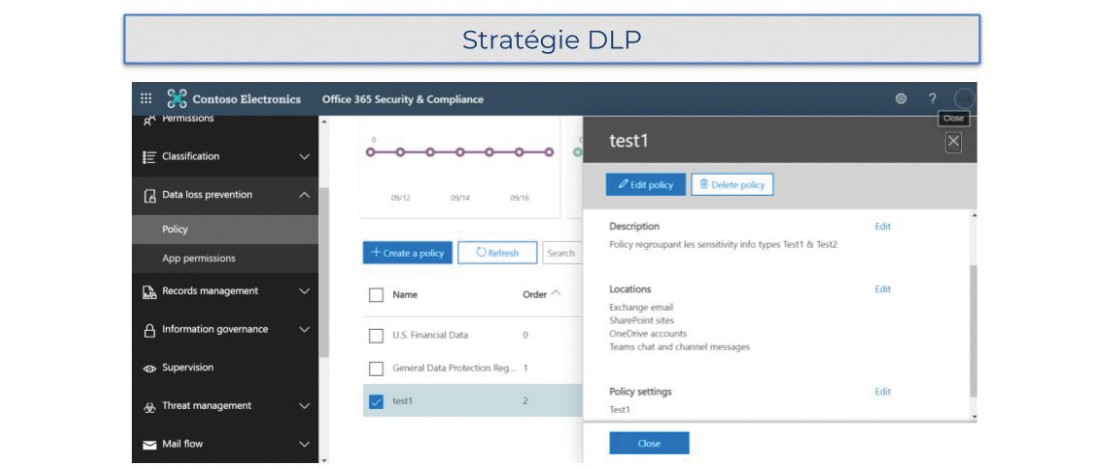
These automatically executed rules restrict the circulation of information, applying an encryption policy to them by preventing exposure of unencrypted sensitive data, whether stored, in transit on the network or on the web. The rules should also be integrated into a global debate about data encryption and classification in an organisation’s overall information system.
The Azure Rights Management service, included in the Microsoft Information Protection solution, completes protection by offering encryption, identity and authorisation strategies so sensitive information is seen only by those authorised to access it.
To obtain end-to-end protection against data loss, surveillance and protection functionalities should be extended to the assets of the information system. Microsoft’s Endpoint Data Loss Prevention (Endpoint DLP) solution detects usage situations and the sharing of sensitive data in the information system to avoid any risky behaviour compromising its integrity.
For Windows 10 managed stations, Microsoft Endpoint DLP offers audit and restriction functions on activities like upload to a cloud service, use of inappropriate browsers, copying to other applications, copying to USB media or network directories, or printing of documents.
4. Investigation
For continued improvement, it is important to investigate internal behaviour contrary to the organisation’s policy (illegal, inappropriate, unauthorised and/or unethical behaviour), check legal aspects linked to data and supervise the process of increasing compliance maturity levels.
For this, Microsoft offers three solutions:
- Insider Risk Management identifies risky human behaviour such as theft or leaking of data. This tool allows analysis and the taking of adequate measures to minimise the organisation’s internal risks.
To ensure that communications comply with the organisation’s standards, the “Communication Compliance” functionality offers a thorough analysis of communications in Microsoft 365, relating to the use of inappropriate expressions (inappropriate or shocking language, contrary to the organisation’s general communication policy, etc.) both internally and externally. Among the most significant areas of compliance are company strategies, risk management, and regulatory compliance.
- Advanced eDiscovery offers a complete solution to the needs of a posteriori investigation, internally and externally, concerning incidents specific to the organisation’s data. It also supports legal teams in managing the depositaries involved, as well as the workflow of lawful storage.
- Azure Sentinel plays the role of SIEM2 and SOAR3 providing supervision that supports and facilitates the collection of actions carried out by the set of users, items of equipment and applications stored in the Cloud or on-premise.
This solution centralises information which can highlight threats across the whole organisation, providing a global tool for detection, visibility and remediation of non-compliance in relation to the policy defined.
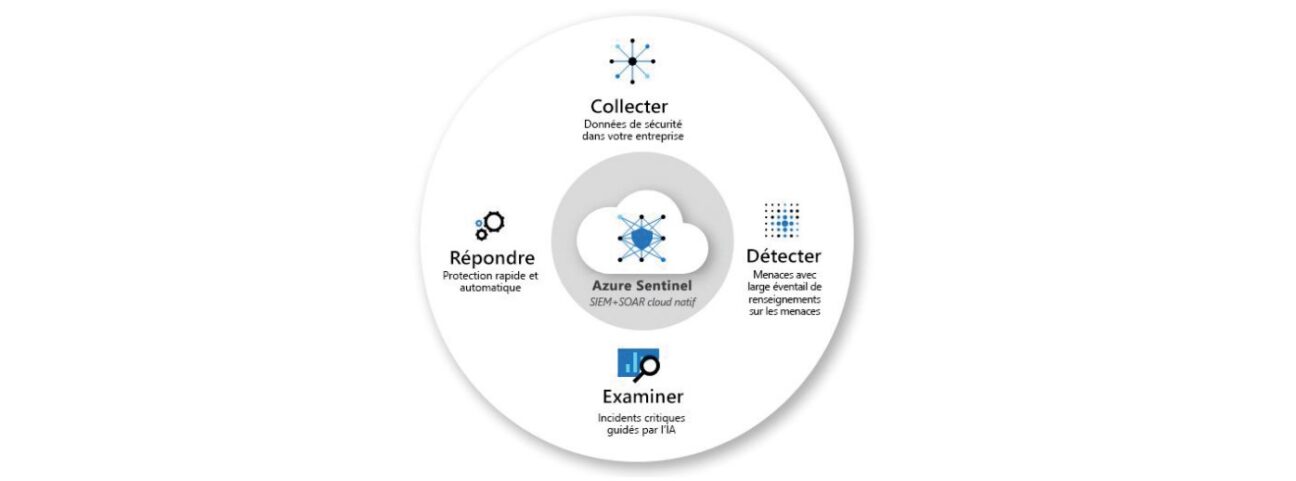
The Sentinel package allows possible inconsistencies with the organisation’s compliance policies to be highlighted, and therfore readjustment of the overall evaluation process of the M365 tenant’s compliance, increasing the level of compliance maturity iteratively.
