Despite the persistence of internal barriers, the regulatory pressure – including the coming into force of GDPR, and the media coverage of major incidents that have had a positive impact, cybersecurity is now being taken into account by the Business, which is starting to acknowledge its value. However, opinions are still very divided on its main contribution, with none of the various proposals of the survey – improving operational efficiency, reducing operating costs, optimising risk management, compliance and enhancing brand image – standing out among business respondents
What is the primary area in which your organization expects IT security to deliver value?
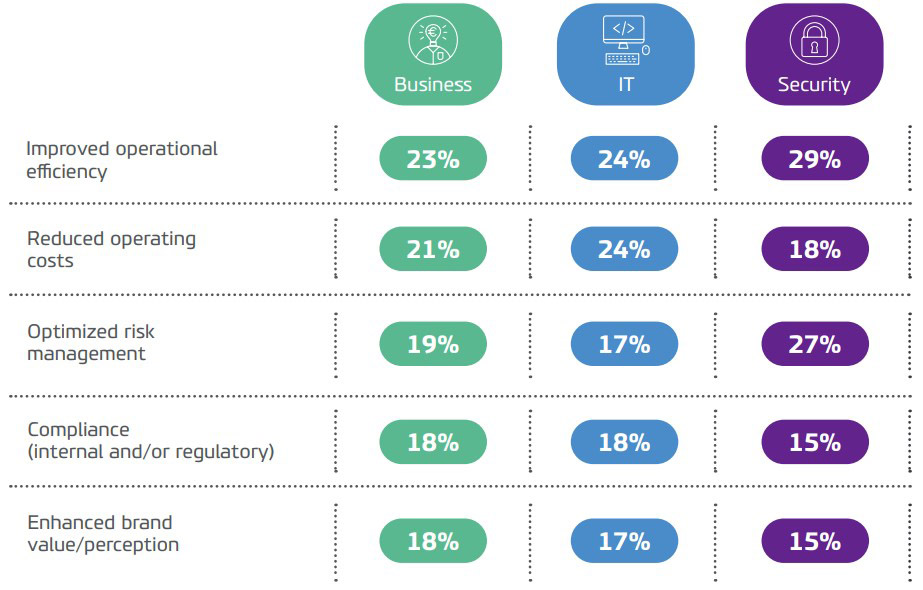
In other words, awareness is still superficial. Security is not deliberately neglected by Business managers, but because they are uncomfortable with the subject and unsure of what it can do for them, they do not consider it a priority and often end up sacrificing it to other issues. In fact, they are the only ones among the profiles surveyed to rank the difficulty of balancing different priorities as one of the top three barriers to improving security
What is mainly limiting your organization’s ability to improve its security?
Business
- Budget constraints
- Skills shortage
- Balancing security priorities with business/productivity priorities
IT
- Fragmentation or lack of integration of security product portfolio
- Budget constraints
- Skills shortage
Security
- Fragmentation or lack of integration of security product portfolio
- Budget constraints
- Skills shortage
However, all the stakeholders unanimously agree on two major challenges:
budgetary constraints and skills shortages. Regarding the first matter, although it is rare to consider ones department sufficiently financed, the lack of funds also reveals that security is not given as much importance in reality as it is in theory. In many cases, only the bare minimum, i.e. what is required by regulations and control authorities, is addressed.
As for the skills shortage, it is probably not so much a question of experts in a particular cybersecurity technology, but rather of having profiles within the business capable of bringing maturity to all organizational levels. Because, as revealed by these results, they are seriously lacking.
